MacAttack
MacAttack is a GUI tool designed for testing and brute forcing your own IPTV stalker portals. This tool is not for hacking purposes. It helps you understand how hackers could exploit vulnerabilities in your portals.
Note: Only use MacAttack on portals you own or have explicit permission to test.
Overview
IPTV stalker portals are commonly shared in IPTV groups across platforms like Telegram, Reddit, and other forums. These portal links typically end in /c/.
MacAttack helps identify unshared and accessible MAC addresses in these portals.
Requirements
- Windows version 8 or higher.
Installation
Download the file MacAttack.exe from the Releases page.
Usage Instructions
Testing stalker portals can take varying amounts of time depending on the portal. Here's how to use the tool effectively:
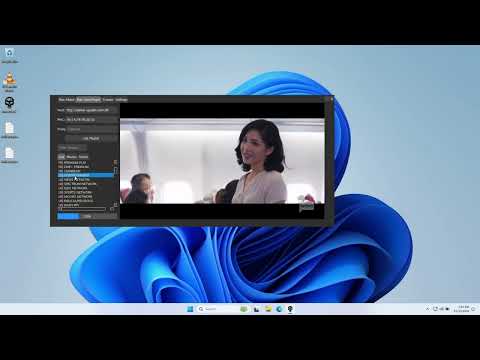
MacAttack Tab
For testing portal security:
- Navigate to the Proxies tab.
- Enable proxies.
- Populate the proxy list with valid proxies. - Go to the MacAttack tab.
- Enter your portal's URL in the provided box.
- Set the desired speed (1-100). - Click Start to begin the test.
Mac VideoPlayer Tab
A modification of the open source project IPTV-MAC-STALKER-PLAYER
For accessing and testing playlists:
- Enter your portal's URL in the first box.
- Input the MAC address in the second box.
- Click Get playlist to retrieve available content.
- Double-click items in the playlist to view them.
Tutorial Video
For a detailed walkthrough, watch this video tutorial. It's a bit outdated now, but still relevant.
Screenshots
The Main Tab
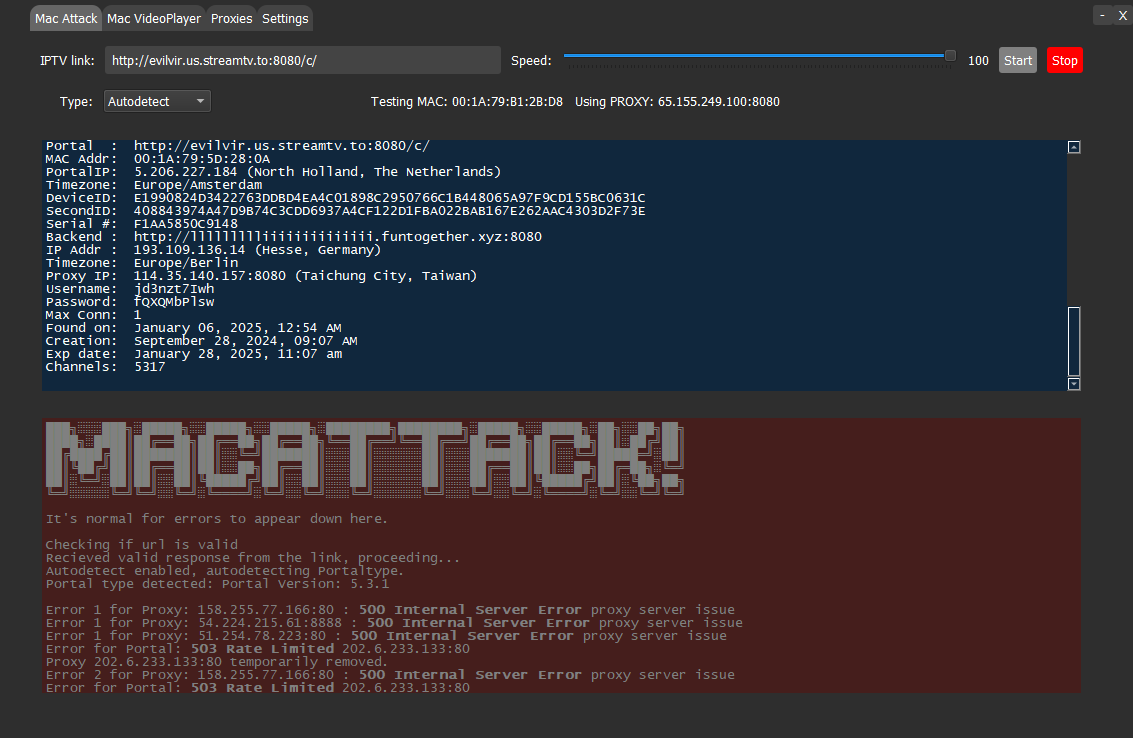
The Videoplayer Tab (Primal is an awesome show, I highly recommend it!)
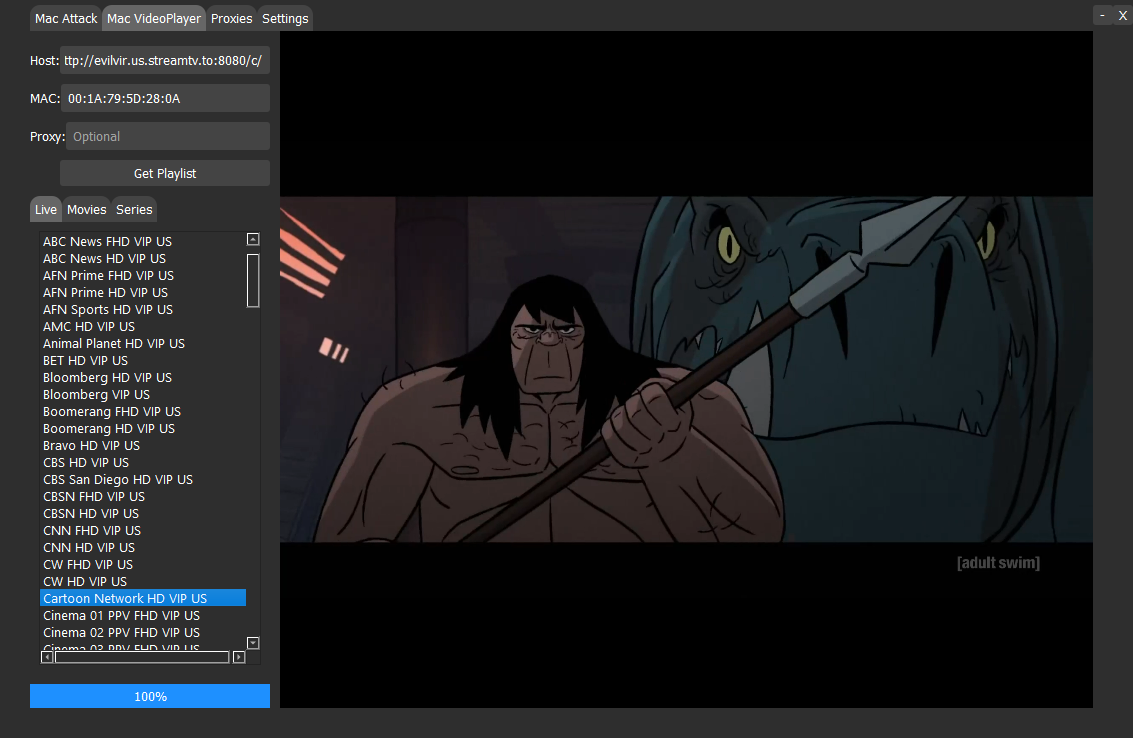
The Proxies Tab
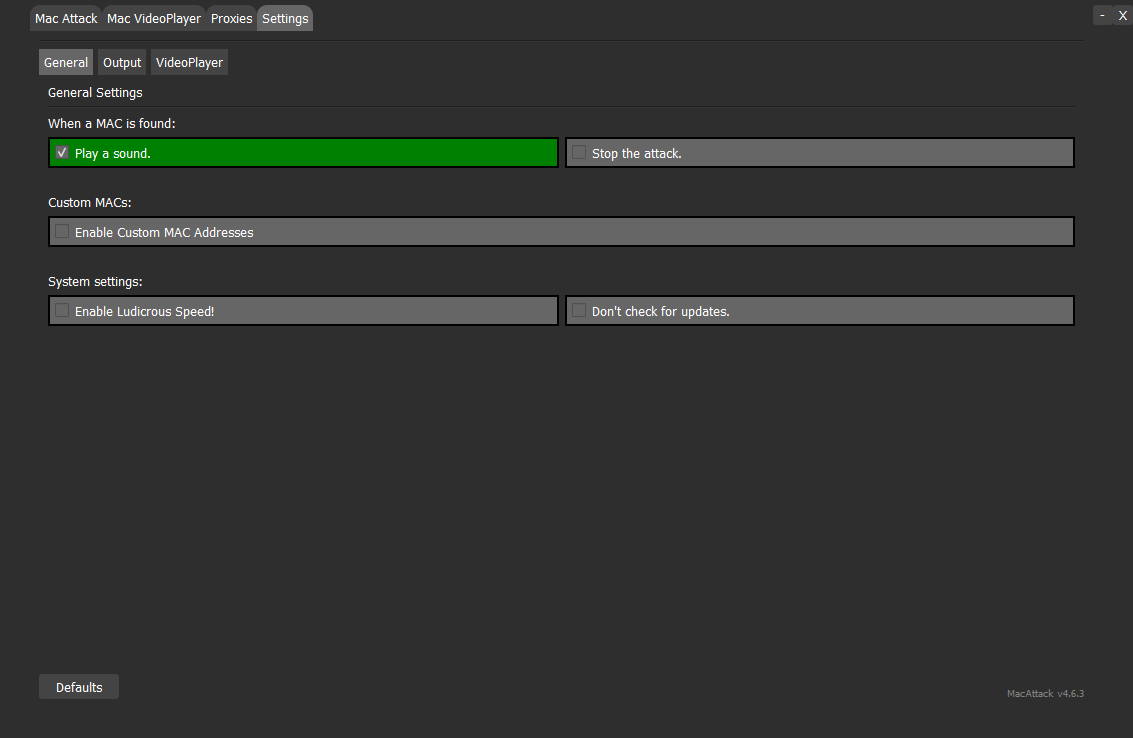
General Settings
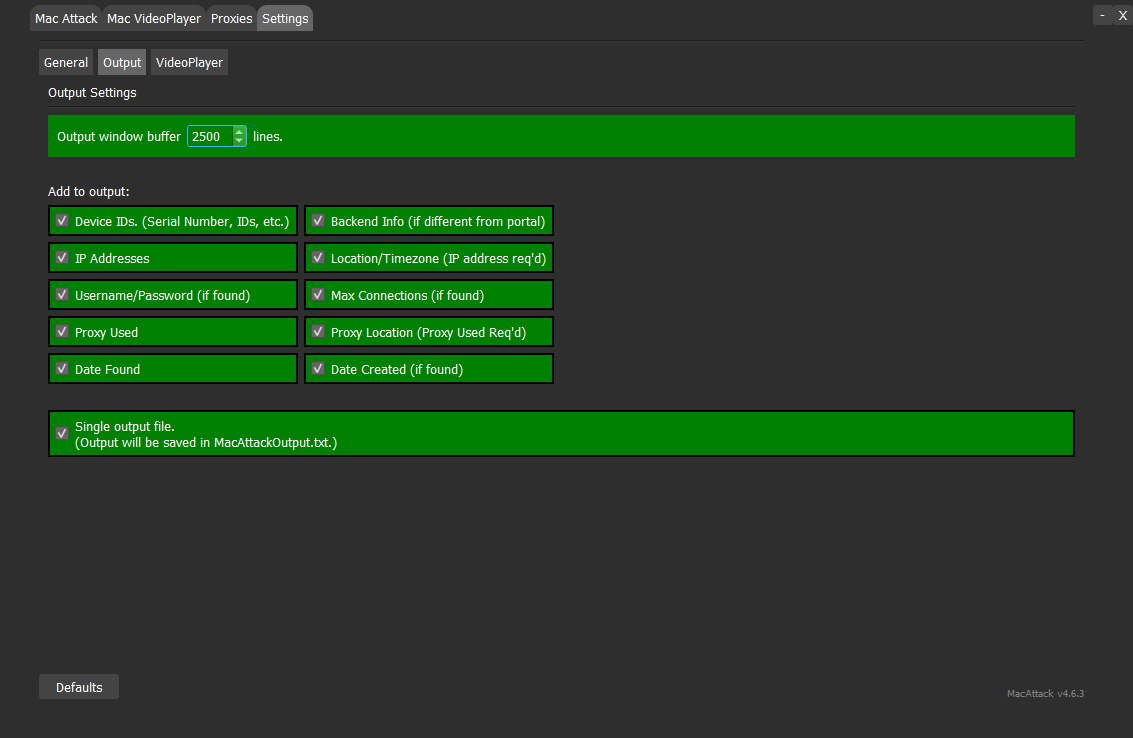
Output Settings
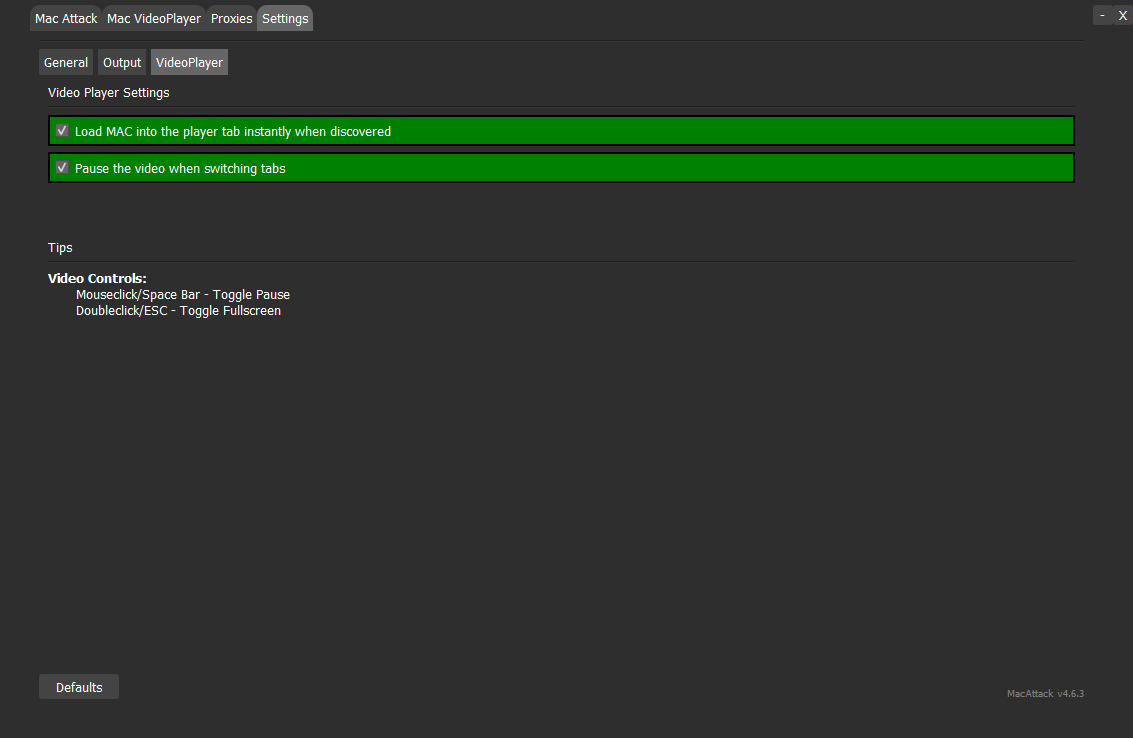
Videoplayer Settings
Disclaimer
MacAttack is strictly a testing tool. Unauthorized use on others' portals may violate laws or terms of service. Always ensure you have permission to test a portal.